The Importance of IoT Penetration Testing
IoT Penetration Testing is a critical process for evaluating the security of Internet of Things (IoT) devices and their associated networks. As IoT devices become increasingly common in homes, industries, and businesses, they introduce unique security challenges. These devices, ranging from smart appliances to wearable tech, often have limited security features and can be vulnerable to attacks. Penetration testing helps identify weaknesses in the device hardware, communication protocols, and software applications that could be exploited by malicious actors.
The testing process involves assessing device vulnerabilities, network security, and the privacy of transmitted data. It also checks for flaws in authentication methods and the integrity of device firmware.
In an era where technology connects us like never before, staying secure in a digital landscape is more crucial than ever. With increasing online interactions, cyber threats have grown in sophistication, targeting individuals, businesses, and organizations alike. Our mission is to help you navigate this connected world with confidence, armed with the tools and knowledge to stay safe.
Key Aspects of IoT Penetration Testing
Key Aspects of IoT Penetration Testing involve a comprehensive assessment of various components that make up an IoT ecosystem, identifying vulnerabilities that could be exploited by attackers. The first aspect is Device Testing, where the physical device itself is examined for security weaknesses, such as hardcoded passwords, insecure firmware, or improper configurations. Network Security is another critical area, focusing on how IoT devices communicate over networks, ensuring that protocols like Wi-Fi, Bluetooth, or Zigbee are secure and do not expose the system to attacks.
Application Layer Security is equally important, as it ensures the mobile or web applications connected to the IoT devices are secure, with proper access controls and data handling. In Firmware and Software Security, testers look for outdated or vulnerable software, ensuring that devices are updated and resilient to attacks. The aspect of Data Privacy and Integrity ensures that any sensitive data, whether in transit or at rest, is properly encrypted and protected. Lastly, Authentication and Access Control testing checks the effectiveness of authentication mechanisms, ensuring that only authorized users can interact with the IoT devices.
Expert Security, Trusted Solutions

We specialize in delivering robust cybersecurity solutions with precision and expertise. From comprehensive assessments to 24/7 monitoring and incident response, our team is committed to safeguarding your business. We understand the unique security needs of each client and work closely to design tailored solutions that protect your digital assets. Whether it’s conducting penetration testing, ensuring regulatory compliance, or providing employee training, Cybivalue is your trusted partner in cybersecurity. Let us handle the complexities of security so you can focus on what matters most—growing your business with confidence.
What makes us special & Why clients choose us?
Projects completed
International Standards
Success Rate
Global Presence
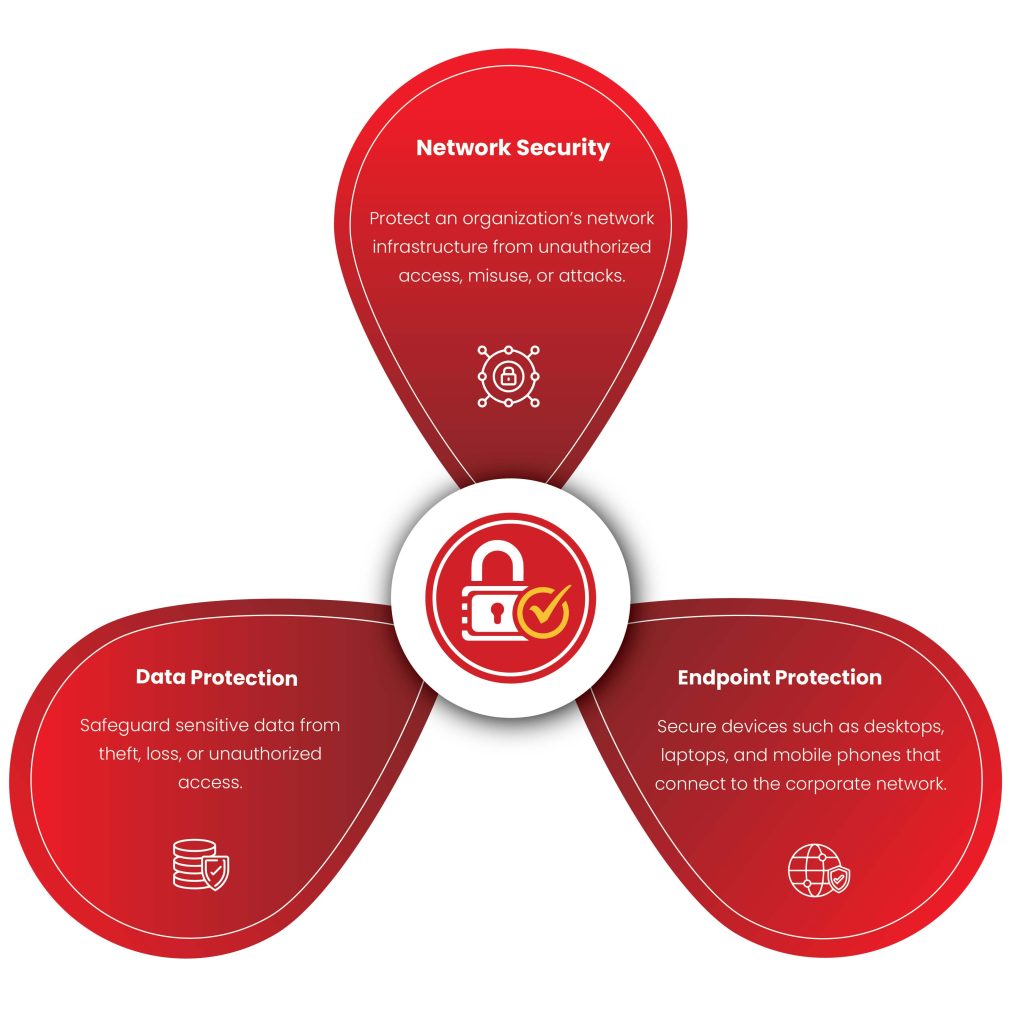
Overview of Critical Cybersecurity Services

1. Network
Security
Protects the network infrastructure from attacks, ensuring that only authorized users can access systems and data.

2. Data
Protection
Involves safeguarding sensitive data from breaches, ensuring confidentiality, integrity, and availability.

3. Incident
Response
A service that focuses on responding to and mitigating the damage caused by cybersecurity incidents or breaches.

4. Cloud
Security
Cloud Security Ensures that data and services hosted on the cloud are secure from potential threats.
Challenges in IoT Penetration Testing
Diverse and Complex Ecosystem
The Diverse and Complex Ecosystem of IoT (Internet of Things) presents significant challenges in ensuring robust security. IoT devices come in various forms, from consumer gadgets like smart thermostats and wearable fitness trackers to industrial machines and smart sensors.
These devices often operate across multiple communication protocols such as Wi-Fi, Bluetooth, Zigbee, and cellular networks, each with its own security requirements and potential vulnerabilities.
Additionally, the vast range of device manufacturers, each with different hardware, software, and security standards, creates a fragmented security landscape. This diversity makes it difficult to implement a one-size-fits-all security solution. Furthermore, IoT devices often have limited computing power, memory, and processing capacity, which restricts the ability to deploy sophisticated security measures.


Limited Resources
Limited Resources in IoT devices present a significant challenge in securing these systems. Many IoT devices are designed to be compact, cost-effective, and energy-efficient, often resulting in limited processing power, memory, and storage capacity. These constraints make it difficult to implement robust security measures such as encryption, advanced firewalls, or real-time threat detection systems. For instance, small devices like smart sensors or wearable tech may not have enough computational resources to run complex security protocols, leaving them vulnerable to attacks.
Additionally, the limited ability to update software or firmware on certain devices means that security vulnerabilities may persist for extended periods, exposing these devices to potential exploits. Manufacturers often prioritize functionality and affordability over security, which can lead to weak default settings, hardcoded passwords, and insecure communication protocols.As the IoT ecosystem grows, addressing these resource limitations is crucial to ensuring the protection of connected devices against evolving cyber threats.
Rapidly Evolving Technology
The rapidly evolving technology behind IoT devices creates a unique challenge in maintaining consistent security. As IoT technology advances at an accelerated pace, new devices, features, and communication protocols are introduced frequently, often outpacing the development of adequate security measures. This constant innovation results in a continuous influx of potential vulnerabilities that can be exploited by cybercriminals.
Furthermore, many IoT devices are deployed without sufficient security assessments, as manufacturers rush to market with the latest innovations. The speed at which these technologies evolve also makes it difficult for organizations and security professionals to keep up with emerging threats, as the attack surface constantly changes. As IoT devices become more interconnected, the potential for large-scale breaches grows, and it becomes even more challenging to anticipate and mitigate risks. Regular testing, updates, and proactive security strategies are essential to adapt to the ever-changing landscape of IoT technology .


Fragmented IoT Security Standards
IoT Penetration Testing is the Lack of Standardization across IoT devices. The IoT industry is still relatively young, and there is no universally accepted set of security standards or best practices for device manufacturers. Different manufacturers use various protocols, hardware, and software, resulting in a highly fragmented ecosystem. This lack of standardization makes it difficult for penetration testers to apply consistent testing methods across all devices.
Additionally, each device may have its own set of security features, vulnerabilities, and configurations, requiring testers to adapt their approach for each unique device. The absence of consistent security guidelines also means that many IoT devices are released with weak security, relying on the manufacturer’s discretion for protection measures. This inconsistency complicates the process of identifying vulnerabilities and ensures that IoT security testing is not as straightforward as it could be with standardized frameworks.



