The Importance of API Penetration Testing
API penetration testing is a crucial process for evaluating the security of application programming interfaces (APIs) that enable communication between different software systems. APIs are widely used in modern web and mobile applications to facilitate data exchange, authentication, and various other services. However, as critical components of application architectures, APIs are often targeted by attackers seeking to exploit vulnerabilities for unauthorized access or data breaches. Penetration testing helps identify weaknesses in the API’s design, functionality, and implementation, ensuring that sensitive data is protected and that the API is secure from potential attacks.
One of the key aspects of API penetration testing is assessing authentication and authorization mechanisms. APIs often handle sensitive data and require proper authentication to ensure that only authorized users can access specific resources. Testers simulate attacks on authentication mechanisms, such as OAuth, API keys, or JWT (JSON Web Tokens), to verify their strength. They check for weaknesses like token expiration issues, improper implementation of user roles, and insufficient access controls that could allow unauthorized access to protected endpoints.
API Security Testing for Vulnerabilities
API penetration testing is a proactive approach to identifying and mitigating security vulnerabilities within the Application Programming Interface (API) layer of an application. APIs serve as the bridge between different software components and external systems, making them prime targets for cyberattacks. During API penetration testing, security experts simulate attacks on an API to evaluate its security defenses and uncover potential weaknesses before malicious actors can exploit them.
The primary goal of API penetration testing is to ensure that APIs are secure from a variety of threats. This includes protecting sensitive data, ensuring that only authorized users can access the API, and preventing attackers from bypassing security measures. The testing process typically includes the identification of common API vulnerabilities such as SQL injection, cross-site scripting (XSS), broken authentication, authorization flaws, and input validation issues. Penetration testers also assess how the API handles rate limiting, session management, and data encryption, ensuring that these mechanisms are properly implemented to guard against attacks like brute force, man-in-the-middle (MitM), and data breaches.
During the testing process, penetration testers often use automated tools to scan for known vulnerabilities, alongside manual testing to identify more sophisticated security flaws. This comprehensive approach helps to uncover both low-hanging fruit vulnerabilities, as well as more complex, harder-to-find weaknesses that could pose a serious threat to the API ecosystem.
Expert Security, Trusted Solutions

We specialize in delivering robust cybersecurity solutions with precision and expertise. From comprehensive assessments to 24/7 monitoring and incident response, our team is committed to safeguarding your business. We understand the unique security needs of each client and work closely to design tailored solutions that protect your digital assets. Whether it’s conducting penetration testing, ensuring regulatory compliance, or providing employee training, Cybivalue is your trusted partner in cybersecurity. Let us handle the complexities of security so you can focus on what matters most—growing your business with confidence.
What makes us special & Why clients choose us?
Projects completed
International Standards
Success Rate
Global Presence
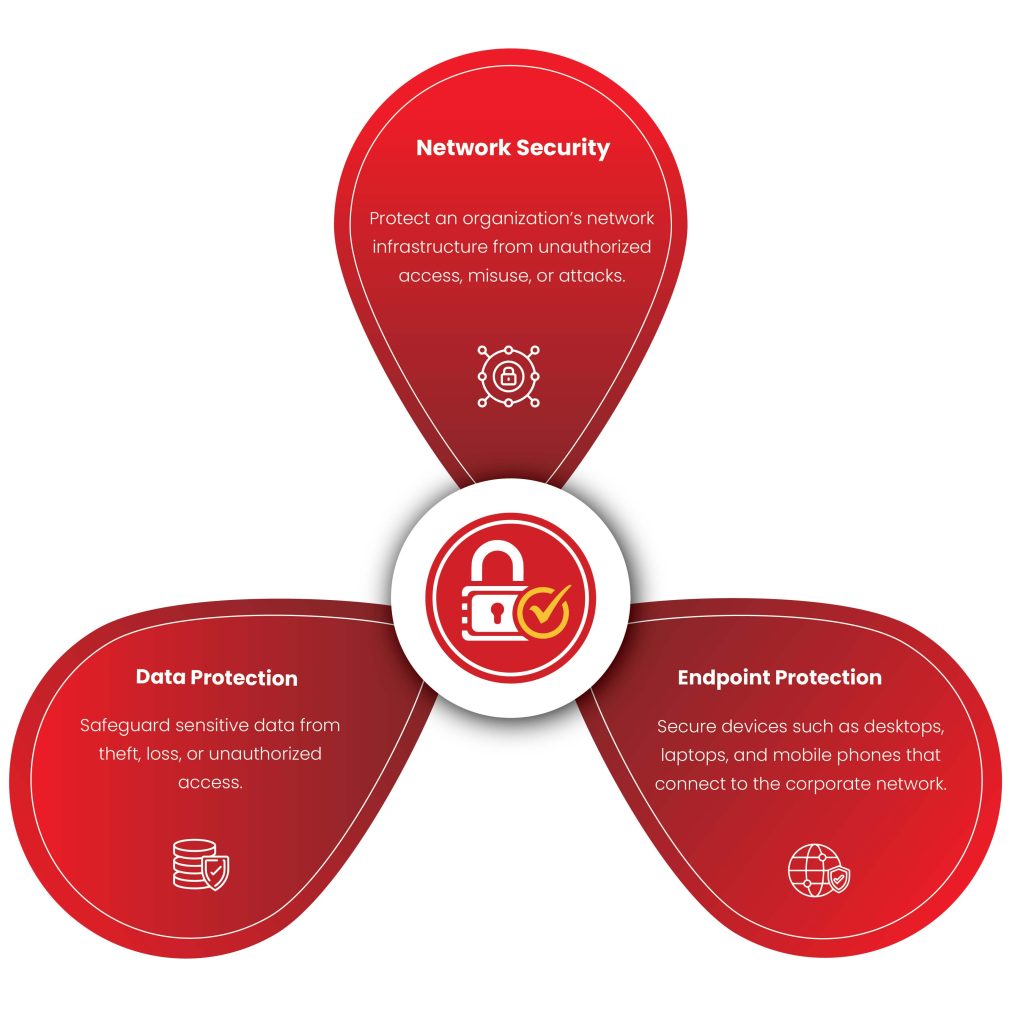
Overview of Critical Cybersecurity Services

1. Network
Security
Protects the network infrastructure from attacks, ensuring that only authorized users can access systems and data.

2. Data
Protection
Involves safeguarding sensitive data from breaches, ensuring confidentiality, integrity, and availability.

3. Incident
Response
A service that focuses on responding to and mitigating the damage caused by cybersecurity incidents or breaches.

4. Cloud
Security
Cloud Security Ensures that data and services hosted on the cloud are secure from potential threats.
Key Pillars of Effective API Penetration Testing
Authentication & Authorization
Authentication and authorization are two of the most critical components of API security, as they determine who can access the API and what actions they can perform. During API penetration testing, these mechanisms are rigorously tested to identify weaknesses that could allow unauthorized access or privilege escalation.
Authentication is the process of verifying the identity of a user or system. It ensures that only authorized individuals or applications can interact with the API. In penetration testing, testers simulate attacks against various authentication mechanisms to evaluate their strength. Common authentication methods include API keys, OAuth, and JWT (JSON Web Tokens). Each method has its own set of vulnerabilities that need to be addressed.
Penetration testers assess if authentication credentials, such as passwords or tokens, are being securely transmitted and stored. They check if multi-factor authentication (MFA) is properly implemented, as this provides an additional layer of security. Testers may also attempt to exploit brute force or credential stuffing attacks to determine if the API is vulnerable to unauthorized login attempts.


Input Validation
Input validation is a critical security measure that ensures data entered into an application or transmitted through an API is correct, secure, and does not pose a risk of exploitation. During API penetration testing, testers evaluate how well an API handles input from users, other systems, or external sources to identify vulnerabilities that could lead to serious attacks, such as SQL injection, Cross-Site Scripting (XSS), or Buffer Overflow.
The process of input validation checks whether the data sent to the API is both accurate and within acceptable parameters. If input is not validated properly, attackers may be able to manipulate it in ways that lead to unauthorized access, data corruption, or even the execution of malicious code. For instance, SQL injection occurs when unsanitized user input is used directly in SQL queries, allowing attackers to manipulate the database by injecting malicious commands.
Rate Limiting & Throttling
Rate limiting and throttling are crucial security mechanisms that protect APIs from abuse and attacks, such as Denial-of-Service (DoS) and Brute Force attacks. During API penetration testing, these mechanisms are evaluated to ensure that they are implemented correctly and provide sufficient protection against malicious users or automated bots attempting to overwhelm the API by sending excessive requests.
Rate limiting is a technique used to restrict the number of requests a user or client can make to an API within a specified period (e.g., 100 requests per minute). This helps to prevent abuse, ensure fair usage, and protect the API from being overwhelmed by too many requests in a short time. If rate limiting is not properly configured, attackers can exploit the API by sending a large volume of requests, potentially causing system slowdowns, service outages, or crashes. Penetration testers simulate high-volume request attacks, such as DoS or brute force attempts, to verify whether the API properly enforces rate limiting and blocks excessive requests. This helps to ensure that legitimate users are not impacted by malicious traffic while preventing potential resource exhaustion.


Data Encryption
Data encryption is a fundamental aspect of securing sensitive information within APIs. It ensures that data remains confidential and protected from unauthorized access, both when it is stored and when it is transmitted. During API penetration testing, evaluating the strength and effectiveness of data encryption mechanisms is crucial to identify potential weaknesses that attackers might exploit to intercept or manipulate sensitive data.
In the context of API security, data encryption primarily focuses on two key areas: data in transit and data at rest.
Data in transit refers to information that is transmitted between the client (e.g., a mobile app, browser, or another service) and the API server. This data is particularly vulnerable to interception, especially when it traverses the public internet. Penetration testers ensure that APIs use strong encryption protocols such as HTTPS (SSL/TLS) to secure communications. They test for potential vulnerabilities like Man-in-the-Middle (MitM) attacks, where an attacker could intercept and alter data in transit.



