-
Request a call back
+91 8310786100
-
Write us
contact@cybivalue.com
-
Book a Consultation
Click Here
We evaluate APIs for vulnerabilities to ensure secure data transmission and prevent unauthorized access. This testing ensures your API integrations are safe from cyber threats.








Identify and mitigate security weaknesses before they become threats. At Cybivalue, our comprehensive Vulnerability Assessment service scans your IT infrastructure, applications, and networks to uncover potential risks. We deliver actionable insights with detailed reports, helping you strengthen your security posture and ensure compliance with industry standards.
Protect your digital assets with Cybivalue’s advanced Web Application Security solutions. We identify and fix vulnerabilities such as SQL injection, cross-site scripting (XSS), and authentication flaws to safeguard your web applications from cyber threats. Our proactive testing and monitoring ensure your applications remain secure, reliable, and compliant.
Secure your APIs against evolving threats with Cybivalue’s API Security Testing services. We perform in-depth assessments to detect vulnerabilities like broken authentication, data exposure, and injection attacks. Our testing ensures your APIs are robust, compliant, and resilient—protecting sensitive data and maintaining seamless system integrations
Cybivalue delivers end-to-end Network Security solutions to protect your IT infrastructure from internal and external threats. We assess, monitor, and fortify your networks with advanced tools and strategies—ensuring data integrity, secure access, and uninterrupted operations across your entire organization.

A cloud penetration test is a type of security testing in which experts perform cyber-attacks on the cloud system. The goal is to find weaknesses and vulnerabilities that hackers may exploit. Cloud systems can serve as the core of vital business processes, so running regular tests is essential to ensure your cloud environment is safe.
For businesses operating in Sharjah , cloud penetration testing is an essential component of a comprehensive cybersecurity strategy. Whether your company is using private, public, or hybrid cloud services, it is crucial to recognize that each cloud model presents its own security challenges. Cloud penetration testing in Sharjah helps identify these vulnerabilities by performing simulated cyberattacks on your cloud infrastructure, giving you a clear picture of potential risks.
By opting for cloud penetration testing, businesses can proactively identify weaknesses in their cloud systems, enabling them to address vulnerabilities before they can be exploited by cybercriminals.
As Japan grows into a major center for innovation and technology, the demand for cloud-based security tests increases in parallel. Businesses are increasingly moving to cloud-based services. However, along with these moves are risks. Cloud settings that are not properly configured, weak authentication systems, and software that is not patched create the opportunity for cybercriminals to take advantage of the system.
Cloud security testing reduces risk by identifying and addressing weaknesses before attackers gain access. It’s not only about compliance; it’s about proactive security. Cloud penetration testing firms in Sharjah provide a range of services to ensure that the cloud is safe from both internal and external threats.
Regularly testing data’s cloud penetration ensures that businesses are conforming to regulations such as GDPR and PCI DSS while also actively safeguarding their operations and data.
The investment in cloud penetration testing offers many benefits to companies in Sharjah:
Conducting cloud penetration tests can help companies spot and fix vulnerabilities before cybercriminals exploit them. Security vulnerabilities, such as improperly configured cloud storage, weak access controls, or insecure APIs, can expose critical data to attackers.
The principal purpose of penetration testing for cloud systems is to enhance the overall security level for your cloud-based infrastructure. Identifying weaknesses in your security procedures and rectifying them lowers the possibility of attacks and ensures that your system remains safe.
Compliance with various security rules and standards is vital for businesses operating in Japan. Regularly conducted cloud security assessments and vulnerability testing will ensure that your company is in compliance with specific industry regulations, such as PCI DSS, GDPR, and ISO 27001, which require companies to take robust security measures.
By identifying weaknesses, early cloud penetration testing can help reduce the chance of attacks on systems and data. This proactive strategy will help reduce costs and protect against damage to your reputation.
By using cloud penetration testing services in Sharjah , companies can address potential risks before they escalate into serious security threats.The type of test conducted depends on the level of complexity of the infrastructure and the specific security requirements of the company. Here are the most commonly used kinds:
This test focuses on identifying weaknesses within the elements of the cloud’s network environment, like routers, firewalls, and switches. Testing for network penetration evaluates the efficacy of security controls such as access segmentation and network controls.
Cloud environments rely on web-based software, meaning penetration testing is a vital procedure component. This test detects weaknesses like SQL injection, cross-site scripting (XSS), and insecure authentication for your cloud-hosted apps.
With the growing usage of APIs for connecting cloud services, API security testing is more crucial than ever. This test examines the APIs of your cloud to find security vulnerabilities, such as insufficient authentication, unsecured data transmission, and flaws in the security of your endpoints.
Social engineering tests are focused on the human aspect. Even the most secure security measures are susceptible to being snuffed out by a manipulated worker to divulge sensitive data. This test simulates phishing and pretexting attacks to determine the effectiveness of your team’s response to threats from social engineering on the cloud.
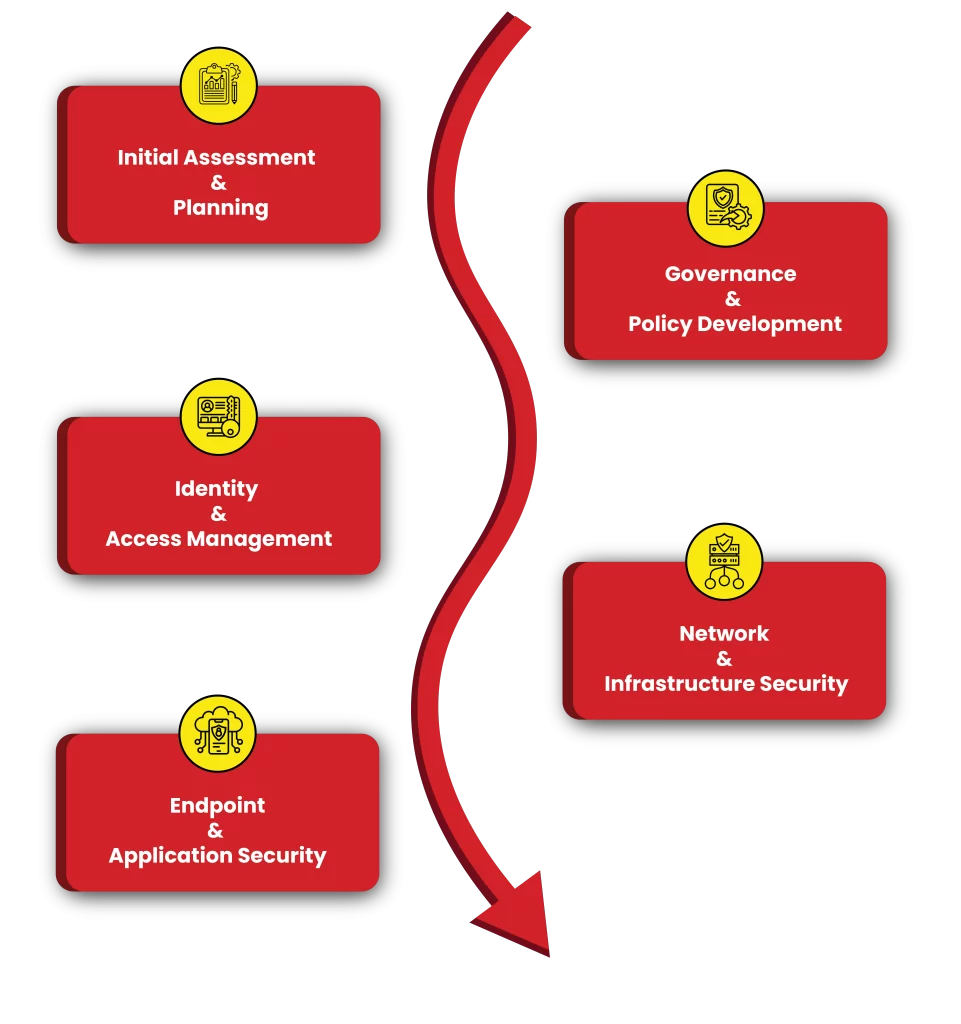
In today’s digital era, ensuring the security of your cloud infrastructure is critical. Cybivalue is a leading provider of cloud penetration testing services in Sharjah, offering a comprehensive approach to safeguarding your cloud environments. With years of expertise and a team of certified professionals, we specialize in identifying vulnerabilities and enhancing cloud security for businesses of all sizes.
The adoption of cloud technologies offers several benefits, but it also opens the door to new security risks. Cloud penetration testing is essential for identifying and mitigating potential vulnerabilities before cybercriminals can exploit them. At Cybivalue, we help businesses in Sharjah stay ahead of the curve by ensuring their cloud infrastructure is secure, compliant, and resilient to cyberattacks.
Many companies in Sharjah are worried about the price of a cloud penetration test. While security is essential, selecting an option with reasonable cost and per-user pricing is crucial.
At Cybivalue, we offer affordable cloud penetration test services with in Sharjah geared towards businesses of all shapes and sizes, from small businesses to huge enterprises. We offer plans that can be scaled to fulfill the security needs of any company and ensure that you don’t need to compromise quality to save money.
The choice of a professional cloud penetration test in Sharjah is vital to ensure a thorough and accurate assessment of your cloud infrastructure. At Cybivalue, we take pride in providing high-quality cloud penetration testing that covers every aspect of cloud security.
Our experts use the latest methods and tools to comprehensively examine your cloud infrastructure and identify possible weaknesses and threats. Our approach to testing for cloud penetration has been designed to not just find vulnerabilities but also provide the information needed to avoid attacks in the future.
When choosing the cloud penetration testing business in Sharjah , be sure to consider these elements:
With Sharjah ‘s growing dependence on cloud services, protecting the cloud infrastructure is now more crucial than ever. Cloud penetration tests can help companies ensure that their infrastructure is protected, compliant, and able to withstand cyberattacks.
At Cybivalue, we provide low-cost, professional, thorough, and expert cloud penetration tests to help businesses protect their cloud infrastructure. Our expert team uses the most advanced methods and tools to ensure the cloud environment is secure from cyber attacks, which will ensure security and peace of mind.
The process of recognizing and assessing potential security risks, vulnerabilities, and threats to the system or network.
Implementing measures such as firewalls, encryption, and access controls to stop cyber threats before they can exploit vulnerabilities.
Monitoring systems for suspicious activities or breaches, using tools like intrusion detection systems (IDS)
Penetration testing simulates real cyberattacks to find and fix security flaws in web applications before hackers can exploit them.
Dubai ’s tech industry relies heavily on web apps, making them prime targets for cyber threats without proper security testing.
Cybivalue uses both static and dynamic testing methods to review code, app behavior, and potential weak points in real-time environments.
Common vulnerabilities include SQL injection, cross-site scripting (XSS), insecure authentication, and poor access controls.
Yes, security testing helps ensure your application meets industry standards like GDPR, HIPAA, and PCI-DSS.
Web apps should be tested regularly—especially after updates or new features—to maintain strong security and user trust.
WhatsApp us




WhatsApp us