-
Request a call back
+91 8310786100
-
Write us
contact@cybivalue.com
-
Book a Consultation
Click Here
We evaluate APIs for vulnerabilities to ensure secure data transmission and prevent unauthorized access. This testing ensures your API integrations are safe from cyber threats.








Identify and mitigate security weaknesses before they become threats. At Cybivalue, our comprehensive Vulnerability Assessment service scans your IT infrastructure, applications, and networks to uncover potential risks. We deliver actionable insights with detailed reports, helping you strengthen your security posture and ensure compliance with industry standards.
Protect your digital assets with Cybivalue’s advanced Web Application Security solutions. We identify and fix vulnerabilities such as SQL injection, cross-site scripting (XSS), and authentication flaws to safeguard your web applications from cyber threats. Our proactive testing and monitoring ensure your applications remain secure, reliable, and compliant.
Secure your APIs against evolving threats with Cybivalue’s API Security Testing services. We perform in-depth assessments to detect vulnerabilities like broken authentication, data exposure, and injection attacks. Our testing ensures your APIs are robust, compliant, and resilient—protecting sensitive data and maintaining seamless system integrations
Cybivalue delivers end-to-end Network Security solutions to protect your IT infrastructure from internal and external threats. We assess, monitor, and fortify your networks with advanced tools and strategies—ensuring data integrity, secure access, and uninterrupted operations across your entire organization.

In today’s digital era, securing network infrastructure and safeguarding data privacy are more critical than ever. Network VA and PT in Haryana play a pivotal role in identifying potential vulnerabilities within a company’s IT environment. With the increasing use of cloud services, remote work setups, and internet-facing applications, it has become essential for organizations to assess their network configurations regularly. A thorough evaluation helps protect sensitive data, prevent unauthorized access, and ensure compliance with industry regulations.
The components of any organization’s cybersecurity strategy. These processes are designed to identify misconfigurations, software, access controls, and other vulnerabilities that could be exploited by cybercriminals.
In Haryana, a leading tech hub in Haryana, businesses are frequently targeted by cyber threats such as phishing, ransomware, and data breaches. Network VA and PT help organizations mitigate these risks by highlighting weak points in their network infrastructure and suggesting improvements. These assessments also contribute to improving system performance and reducing operational downtime by proactively identifying and addressing threats before they can be exploited.
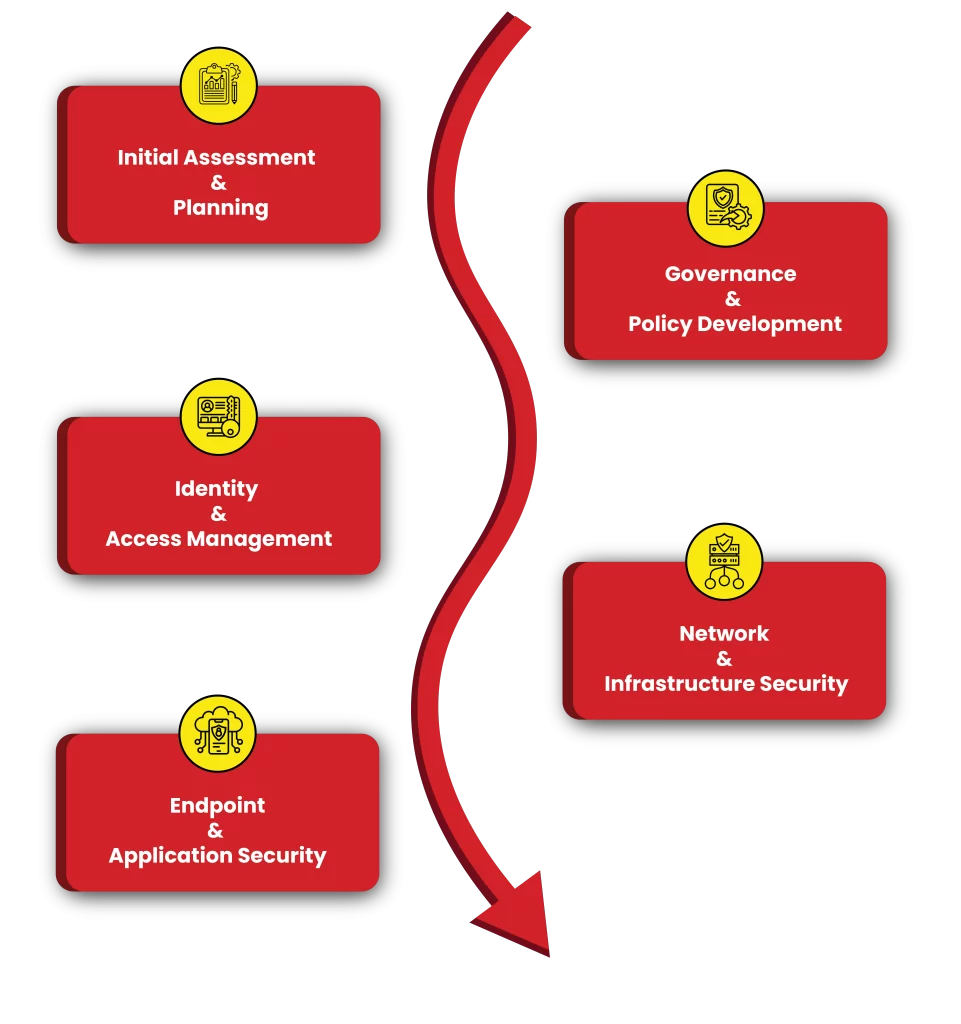
Network VA and PT typically involve several well-defined steps to ensure thorough security evaluation:
The process begins by mapping the entire network and identifying all connected assets, including routers, switches, firewalls, servers, and endpoints. This step provides a complete view of the network’s attack surface.
Security experts then review existing network configurations, firewall rules, access control policies, and segmentation settings. The goal is to ensure that these configurations align with security best practices and regulatory requirements.
Automated tools are used to scan the network for known vulnerabilities. This is followed by manual penetration testing to simulate real-world attacks, helping to uncover deeper, less obvious security flaws that automated tools might miss.
A comprehensive report is generated, detailing identified vulnerabilities, risk levels, and suggested remediation steps. The report provides a prioritized action plan to help the organization quickly address the most critical issues.
Once remediation steps are implemented, a follow-up assessment may be conducted to verify that the vulnerabilities have been resolved. Continuous monitoring and periodic testing are encouraged to maintain a strong security posture.
Organizations may encounter several challenges. One of the key difficulties is the complexity of modern network environments, which often include a combination of on-premise infrastructure, cloud services, and integrations. Ensuring that all network rules and systems are securely configured can be time-consuming and requires a comprehensive understanding of traffic flows and access control mechanisms.
Another challenge is the lack of standardized configurations across different network platforms in many organizations, leading to potential vulnerabilities. Ensuring uniformity in configuration settings is critical for strengthening security and streamlining the assessment process.
Moreover, frequent changes in regulatory standards can create confusion for organizations trying to stay compliant. A Network VA and PT in Haryana must account for these changes to ensure that configurations remain in line with the latest security and compliance requirements.
The process of recognizing and assessing potential security risks, vulnerabilities, and threats to the system or network.
Implementing measures such as firewalls, encryption, and access controls to stop cyber threats before they can exploit vulnerabilities.
Monitoring systems for suspicious activities or breaches, using tools like intrusion detection systems (IDS)
Network VA and PT should be conducted at least annually or whenever there are major changes in network architecture, applications, or security policies.
Yes, assessments can be scheduled during non-peak hours or use non-intrusive scanning methods to avoid any disruption to operations.
Typical issues include open ports, outdated software, misconfigured firewalls, weak access controls, and vulnerabilities.
These assessments should be performed by qualified cybersecurity professionals with expertise in network, penetration testing, and compliance standards.
Yes, many compliance frameworks regular network assessments as part of ongoing risk management.
Network VA focuses on IT systems, data networks, and endpoints, while OT security testing is centered around industrial control systems and ensuring operational continuity.
WhatsApp us




WhatsApp us