-
Request a call back
+91 8310786100
-
Write us
contact@cybivalue.com
-
Book a Consultation
Click Here
We evaluate APIs for vulnerabilities to ensure secure data transmission and prevent unauthorized access. This testing ensures your API integrations are safe from cyber threats.








Identify and mitigate security weaknesses before they become threats. At Cybivalue, our comprehensive Vulnerability Assessment service scans your IT infrastructure, applications, and networks to uncover potential risks. We deliver actionable insights with detailed reports, helping you strengthen your security posture and ensure compliance with industry standards.
Protect your digital assets with Cybivalue’s advanced Web Application Security solutions. We identify and fix vulnerabilities such as SQL injection, cross-site scripting (XSS), and authentication flaws to safeguard your web applications from cyber threats. Our proactive testing and monitoring ensure your applications remain secure, reliable, and compliant.
Secure your APIs against evolving threats with Cybivalue’s API Security Testing services. We perform in-depth assessments to detect vulnerabilities like broken authentication, data exposure, and injection attacks. Our testing ensures your APIs are robust, compliant, and resilient—protecting sensitive data and maintaining seamless system integrations
Cybivalue delivers end-to-end Network Security solutions to protect your IT infrastructure from internal and external threats. We assess, monitor, and fortify your networks with advanced tools and strategies—ensuring data integrity, secure access, and uninterrupted operations across your entire organization.

In today’s hyper-connected digital world, organizations face an increasing number of cybersecurity threats. From sophisticated ransomware to subtle social engineering attacks, the threat landscape continues to evolve rapidly. Traditional defensive measures, while necessary, are often not enough. To stay ahead of cyber adversaries, many companies are turning to a more proactive and comprehensive approach: red teaming. For those in Mozambique, a red teaming service in Mozambique can provide valuable insights into potential security weaknesses and offer tailored solutions to enhance defense strategies.
Red teaming is a security testing methodology where a group of ethical hackers, known as the “red team,” simulates real-world attacks on an organization’s systems, networks, or personnel. The goal is not just to find technical vulnerabilities but also to test the organization’s overall detection, response, and defense mechanisms. Unlike standard penetration testing, which focuses on specific systems or known vulnerabilities, red teaming is broader, more creative, and mimics the tactics, techniques, and procedures (TTPs) of actual threat actors.
One of the main advantages of red teaming is its ability to uncover blind spots. While internal teams may be confident in their security controls, a red team can expose weaknesses that go unnoticed in routine audits or automated scans. These might include gaps in incident response, poor security awareness among staff, misconfigured systems, or vulnerabilities in third-party integrations.
Red teaming exercises often combine a variety of attack vectors. This could involve social engineering tactics such as phishing emails or phone calls, physical breaches like tailgating into restricted areas, or digital exploits targeting servers and databases. The red team operates covertly, often without the knowledge of the broader security team, to see how effectively an organization can detect and respond in real time.
As cyber threats continue to grow in sophistication, the need for specialized security testing services like red teaming is becoming critical. In a tech hub like Mozambique, where the IT and startup ecosystems are thriving, companies are especially keen on ensuring that their security measures can withstand real-world attacks. Engaging a red teaming service in Mozambique can help organizations prepare for complex attack scenarios and avoid the costly consequences of a security breach.
Red teaming is not just about finding weaknesses but also about fostering a culture of security across the organization. It encourages cross-functional collaboration between IT, HR, and physical security teams, ensuring comprehensive defense measures are in place. Moreover, it helps identify gaps in incident response, allowing organizations to better understand how well they can react to an attack and recover in a timely manner. red teaming provides invaluable insights that cannot be gained through traditional assessments. By thinking like the adversary, organizations can identify their true weaknesses and take meaningful steps to protect their most critical assets. With Mozambique emerging as a cybersecurity hub, the availability of expert red teaming services is more prominent than ever, helping businesses build stronger defenses against a variety of cyber threats.
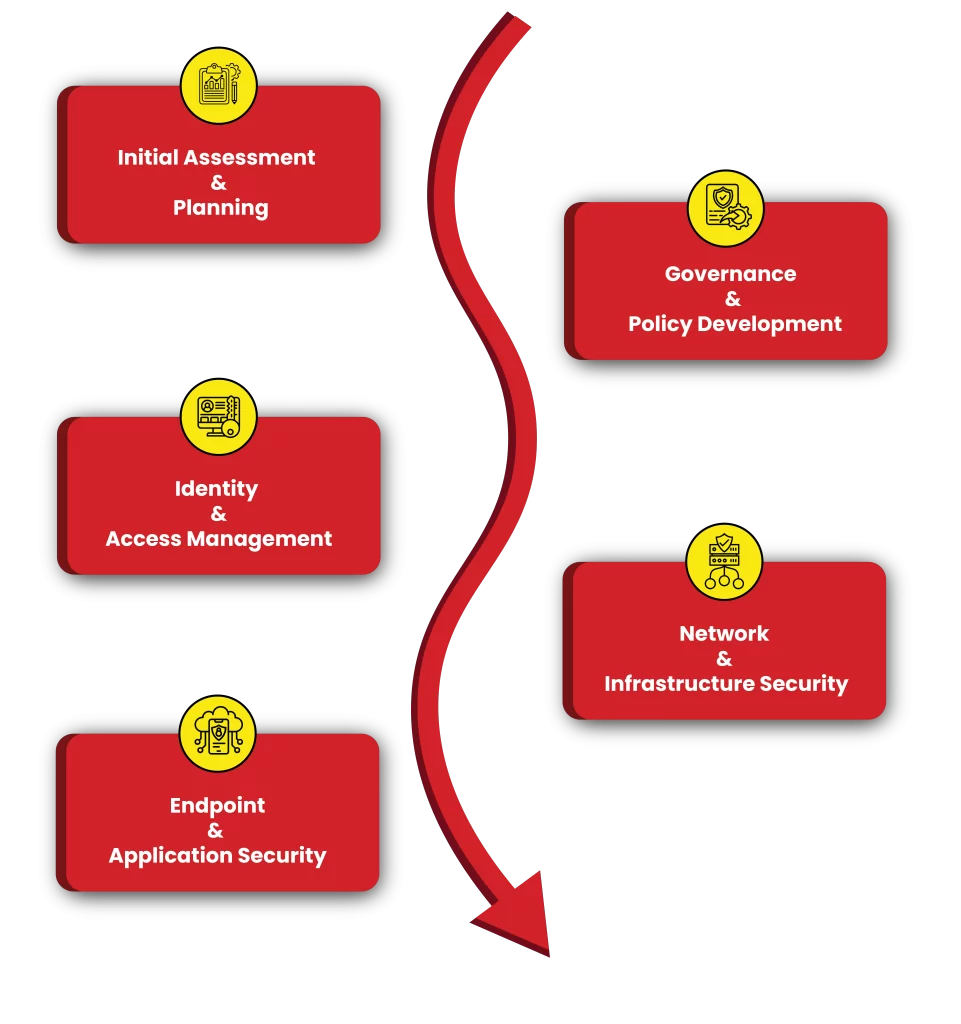
The process of recognizing and assessing potential security risks, vulnerabilities, and threats to the system or network.
Implementing measures such as firewalls, encryption, and access controls to stop cyber threats before they can exploit vulnerabilities.
Monitoring systems for suspicious activities or breaches, using tools like intrusion detection systems (IDS)
Red teaming involves simulating real-world attacks to assess an organization’s security and response.
Red teaming covers broader attack strategies, while penetration testing focuses on specific vulnerabilities.
It helps identify hidden vulnerabilities and strengthens both technical defenses and response mechanisms
The duration can range from a few days to several weeks, depending on the scope of the engagement.
Red teaming simulations include social engineering, phishing, and digital or physical breaches.
Red teaming should be conducted by experienced, independent cybersecurity professionals with expertise in offensive tactics
WhatsApp us




WhatsApp us