-
Request a call back
+91 8310786100
-
Write us
contact@cybivalue.com
-
Book a Consultation
Click Here
We evaluate APIs for vulnerabilities to ensure secure data transmission and prevent unauthorized access. This testing ensures your API integrations are safe from cyber threats.








Identify and mitigate security weaknesses before they become threats. At Cybivalue, our comprehensive Vulnerability Assessment service scans your IT infrastructure, applications, and networks to uncover potential risks. We deliver actionable insights with detailed reports, helping you strengthen your security posture and ensure compliance with industry standards.
Protect your digital assets with Cybivalue’s advanced Web Application Security solutions. We identify and fix vulnerabilities such as SQL injection, cross-site scripting (XSS), and authentication flaws to safeguard your web applications from cyber threats. Our proactive testing and monitoring ensure your applications remain secure, reliable, and compliant.
Secure your APIs against evolving threats with Cybivalue’s API Security Testing services. We perform in-depth assessments to detect vulnerabilities like broken authentication, data exposure, and injection attacks. Our testing ensures your APIs are robust, compliant, and resilient—protecting sensitive data and maintaining seamless system integrations
Cybivalue delivers end-to-end Network Security solutions to protect your IT infrastructure from internal and external threats. We assess, monitor, and fortify your networks with advanced tools and strategies—ensuring data integrity, secure access, and uninterrupted operations across your entire organization.

Evaluating the security of industrial control systems is known as ICS security testing in Sharjah.Transportation, water treatment, electricity grids, and other industrial activities are all monitored and managed by ICS.These systems frequently have direct control over physical operations, and if they are compromised, there may be major service interruptions, monetary losses, or even fatalities.
Cyberattacks on these systems are simulated via ICS security testing to identify weaknesses, assess their potential impact, and provide training solutions. It is essential for any company operating in these areas to ensure their security through testing due to the critical role that ICS play in day-to-day life.
Security for SCADA systems, a subset of ICS, is the main goal of Supervisory Control and Data Acquisition (SCADA security testing in Sharjah). SCADA systems are utilized for real-time remote monitoring and control of industrial processes. These systems are essential to sectors including industry, utilities, oil & gas, and energy production.
Due to their interdependence and reliance on networks, SCADA systems’ security are growing at risk. Remote hacking efforts could result from SCADA system vulnerabilities, giving adversaries the opportunity to take control of critical systems or interrupt regular operations. SCADA security testing aims to identify these vulnerabilities in order to avoid cyberattacks before they have an opportunity to cause harm.
SCADA penetration testing in Sharjah Exploits potential flaws and vulnerabilities by simulating cyberattacks on SCADA systems. To make sure that these systems are adequately safeguarded against contemporary cyberthreats, it is an essential step.
Businesses must use penetration testing for SCADA systems to make sure that their systems are safe from internal and external threats.
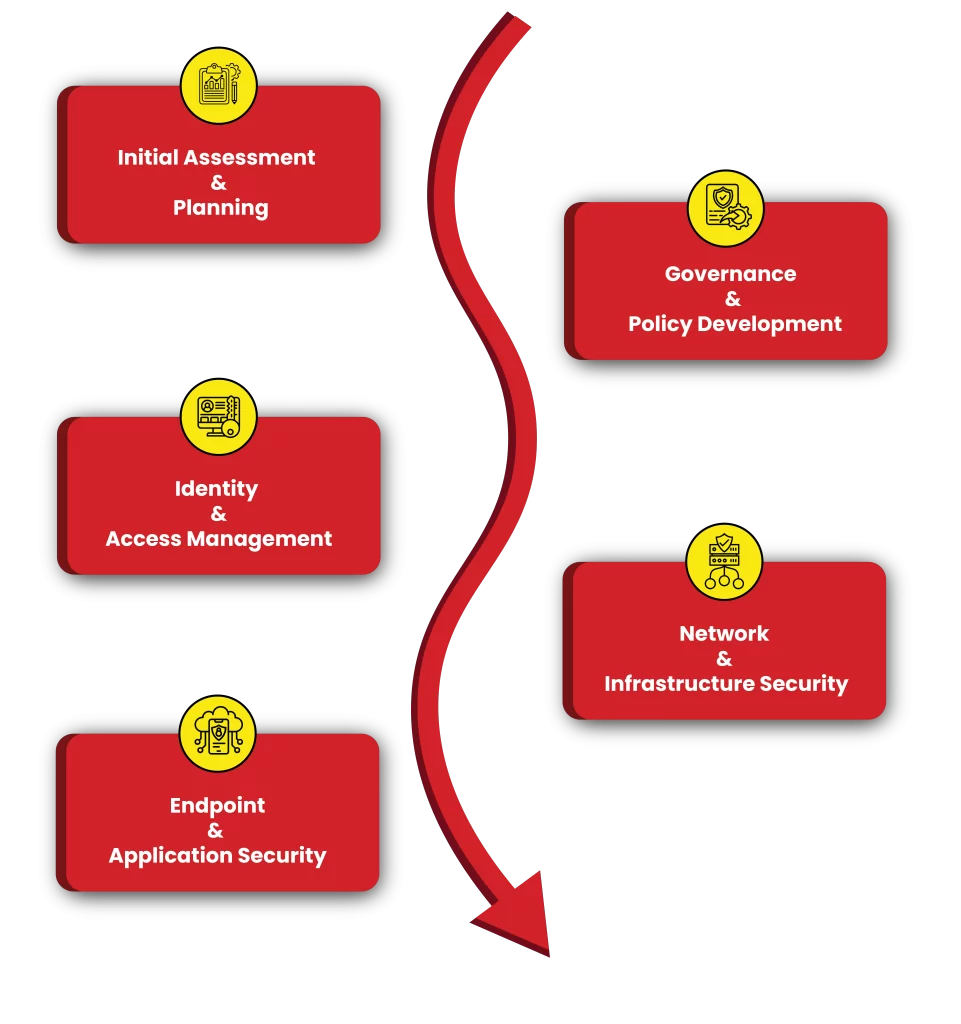
Industrial Control Systems testing in Sharjah Emphasizes assessing the security of the larger ICS infrastructure, which consists of the software and hardware elements that regulate industrial processes. By ensuring that these vital systems are safe from cyberattacks, this testing lowers the possibility of operational interruptions, monetary loss, and safety risks.
ICS testing includes the evaluation of various components such as:
Organizations in Sharjah May make sure that their systems are not just resilient against changing cyber threats but also comply with industry requirements by regularly performing ICS testing.
For your industrial control systems to be secure, selecting the best ICS penetration testing firms in Sharjah is essential. Expert penetration testing services for ICS and SCADA systems are offered by specialized companies like Cybivalue, which use cutting-edge tools and methodologies to resemble actual breaches.
Sharjah SCADA vulnerability testing focuses on identifying and addressing SCADA system security vulnerabilities.SCADA system vulnerabilities can include unpatched firmware, outdated software, and unsafe communication protocols, to name a few.
Businesses can find these flaws and put in place efficient defenses against cyberattacks by regularly testing for SCADA vulnerabilities.
A variety of solutions are included in Sharjah’s ICS cybersecurity services, which are intended to defend industrial control systems against online attacks. These services include risk management, penetration testing, vulnerability assessments, and ongoing ICS network and device monitoring.
Your ICS systems will always be safe, compliant, and resistant to cyberattacks if you work with a respectable cybersecurity company.
SCADA network security testing in Sharjah emphasizes protecting the networks of communications that link SCADA systems to control centers and other industrial equipment. These networks are an essential part of ICS security since they are frequently the target of cybercriminals.
Businesses may guarantee the confidentiality and integrity of their SCADA networks and avoid data breaches and unwanted access by conducting SCADA network security testing.
ICS risk assessment in Sharjah is a proactive method for locating, assessing, and reducing ICS-related risks. This evaluation offers a plan for safeguarding vital infrastructure and assists companies in comprehending the possible risks to their systems.
To make sure of the continuous security and resilience of Sharjah’s vital infrastructure, an ICS risk assessment is a necessary first step.
When it comes to choosing the best ICS security testing companies in Sharjah, Find out a company that specializes in ICS/SCADA security. From vulnerability assessments to comprehensive penetration testing and incident response services, a trustworthy partner will provide customized solutions.
ICS/SCADA security audit in Sharjah is an in-depth review of the security posture of your SCADA and ICS systems.Audits verify compliance and pinpoint opportunities for improvement by comparing your systems to industry standards and best practices.
ICS security testing services in Sharjah provide all-inclusive solutions to defend your vital infrastructure against online attacks. These services include anything from risk management and security monitoring to vulnerability assessments and penetration tests.
At Cybivalue, we specialize in providing ICS/SCADA security testing services in Sharjah. At Cybivalue, we specialize in providing ICS/SCADA security testing services in Sharjah. Using state-of-the-art tools and techniques, our team of experts will identify vulnerabilities in your SCADA and ICS systems and help you implement robust security solutions. Whether you need ongoing cybersecurity support, penetration testing, or vulnerability assessments, Cybivalue has the expertise to keep your critical infrastructure secure.
Put your SCADA and ICS systems in good hands with Cybivalue. Please contact us immediately for more information on how we can help you protect your business from cyberattacks.
The process of recognizing and assessing potential security risks, vulnerabilities, and threats to the system or network.
Implementing measures such as firewalls, encryption, and access controls to stop cyber threats before they can exploit vulnerabilities.
Monitoring systems for suspicious activities or breaches, using tools like intrusion detection systems (IDS)
Cybivalue is the practice of protecting systems, networks, and data from cyber threats, ensuring confidentiality, integrity, and availability of information.
Phishing: Fraudulent attempts to steal information via deceptive messages.
Ransomware: Malware that locks systems and demands ransom for access.
Data breaches: Unauthorized access to sensitive information.
Sectors like healthcare, finance, retail, government, and education are common targets due to their valuable data and potential vulnerabilities.
Endpoint security refers to securing individual devices (like laptops, smartphones, and desktops) that connect to a network, preventing them from becoming entry points for cyberattacks.
AI helps in threat detection, predictive analytics, and automating responses to security incidents, making systems more proactive and efficient.
AI helps in threat detection by analyzing vast amounts of data, identifying patterns, and predicting potential attacks. It also automates responses to known threats.
Social engineering involves manipulating individuals into divulging confidential information, such as passwords or banking details, often through deception.
Keep operating systems and software updated.
Install antivirus programs.
Use a combination of upper and lower case letters, numbers, and special characters. Avoid using personal information and use unique passwords for every account.
WhatsApp us




WhatsApp us